Overview
When trying to use Email Multifactor Authentication (MFA) with an Enterprise connection that uses OpenID Connect (OIDC), the following error is observed:
No MFA factors enabled for enrollment
Applies To
- Email MFA
- Enterprise connections
Cause
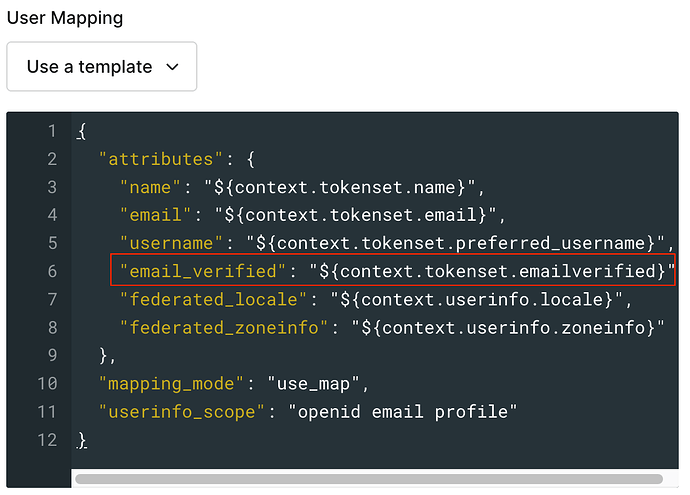
A possible cause of this error is that the email_verified property is not passed from the Enterprise Connection Identity Provider, causing the property to be set to False. See When does Auth0 set emails as verified? for more details.
Solution
Create an email_verified custom claim on the IdP so it sends the claim in the id_token. If possible, name the claim email_verified so no mapping is required on the Auth0 side. If the value of this property is True, the user profile will be marked as verified, and email MFA can be used.
NOTE: If the claim cannot be called email_verified for any reason, then any variation can be used and then mapped on the Auth0 side to email_verified.
See below example of a custom claim created on a third-party IdP when using Open ID Connect (OIDC) that does not match the Auth0 property exactly:
Mapping it to the Auth0 connection so it matches: