Overview
This article explains why the following error occurs when attempting to authenticate with an Azure Active Directory (Azure AD) connection via Auth0 after configuring an application in Azure AD:
- “error”: { “message”: “failed to obtain access token”, “oauthError”: “invalid_request”, “payload”: “{"error":"invalid_request","error_description":"AADSTS50146: This application is required to be configured with an application-specific signing key. It is either not configured with one, or the key has expired or is not yet valid.”, “type”: “request-error” }
The following steps reproduce the issue:
- Configure an application in Azure AD with the necessary permissions.
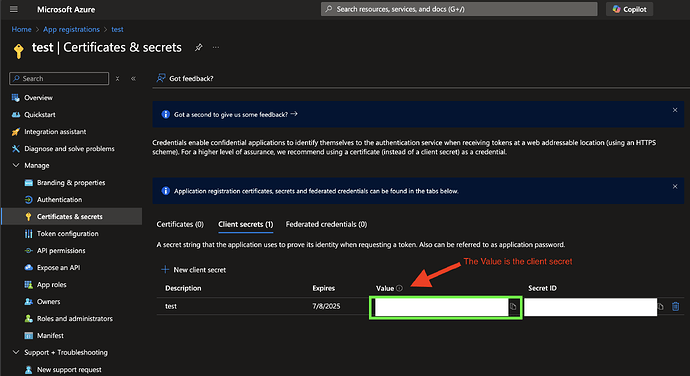
- Obtain a Client Secret from Azure AD and ensure it is active and correctly configured.
- Configure the Auth0 application with the Client ID and Client Secret from Azure AD (Entra ID).
- Attempt to authenticate the application through Auth0.
Applies To
- Error “AADSTS50146”
- Azure AD (Entra ID) Connection
- Windows Live Social Connection
Cause
A misconfiguration of the application on the Azure AD (Entra ID) side causes this error. The error might also occur due to a misconfigured Client Secret.
Solution
To address the issue:
- Refer to the Auth0 Troubleshooting documentation for Azure AD (Entra ID) for additional details regarding a misconfigured Client Secret.
- For issues related to Azure AD (Entra ID) configuration, contact Microsoft support.