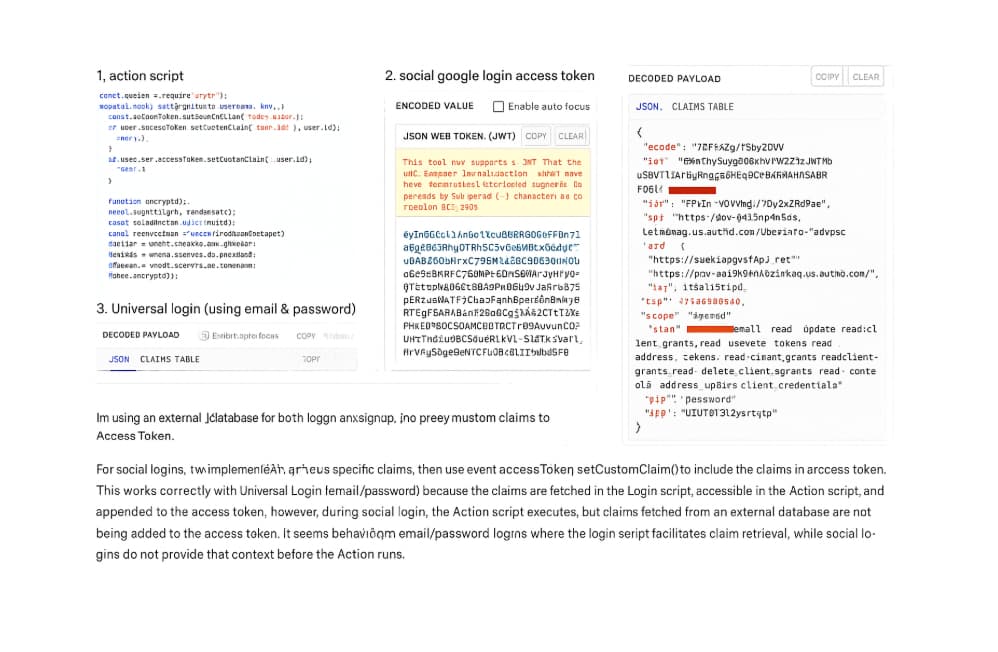
Hello Auth0 Support,
I am facing an issue where custom claims are not being added to the access token during social login (Google) using an Auth0 Post Login Action script. This same setup works perfectly for Universal Login (email & password).
Setup
- Auth0 Action: Post Login
- External Database: Used for both login & signup
- Social Login: Google (via Auth0 connection)
- Universal Login: Username/password (working fine)
- Access Token: Expected to have custom claims (e.g.,
role,user_id, etc.)
What Works (Universal Login Flow)
When users log in via Universal Login (email/password):
- The Action script successfully queries our external DB.
- The DB returns user-specific data.
- Claims are set via
event.accessToken.setCustomClaim(). - These claims appear in the access token as expected.
What Fails (Google Social Login Flow)
When users log in via Google Social Login:
- The same Action script runs.
- The external DB is queried using
event.user.email. - No custom claims appear in the access token.
- It seems
event.usermay be incomplete or uninitialized at the time of execution.
Reproduction Steps
- Configure PostLogin Action to fetch user data from external DB and set custom claims.
- Trigger login via:
- Universal Login → custom claims present in access token.
- Google Social Login → custom claims missing from access token.
Action Script (Example Snippet)
jsCopyEditexports.onExecutePostLogin = async (event, api) => { try { const email = event.user.email; // Call our external DBconst userData = await getUserFromExternalDB(email); if (userData) { api.accessToken.setCustomClaim("app_metadata.role", userData.role); api.accessToken.setCustomClaim("app_metadata.user_id", userData.userId); } } catch (err) { console.log("Error fetching user data:", err); }};
Screenshots
Questions
- Why are custom claims missing in the access token during social login?
- Is there a timing/initialization difference between Universal and Social login for the Action script?
- Is there a recommended workaround to ensure external user data is fetched and custom claims are added for social logins?
Please let me know if any logs, full code, or additional debugging information is needed. I appreciate your help in resolving this.
Thanks,