khushbu
December 17, 2025, 10:54am
1
Hi team,
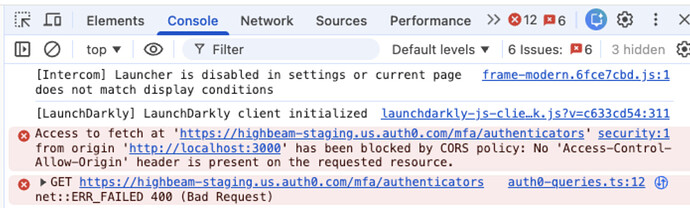
We are calling the list all authenticators api and facing the following error:
Access to fetch at ‘https://highbeam-staging.us.auth0.com/mfa/authenticators ’ from origin ‘http://localhost:3000 ’ has been blocked by CORS policy: No ‘Access-Control-Allow-Origin’ header is present on the requested resource.
listAuthenticators: {
queryKey: ["listAuthenticators"],
queryFn: async () => {
const mfaToken = await getMfaToken();
return auth0Api
.get<AuthenticatorRep[]>("mfa/authenticators", {
headers: {
Authorization: `Bearer ${mfaToken}`,
},
})
.json();
},
},
The code has correct mfa token as well.
The same was working earlier from the frontend. We are wondering if anything changed in last one month at auth0’s end?
How can we get it to work again from FE?
1 Like
khushbu
December 19, 2025, 4:46pm
3
We took the above mentioned api to BE and it worked. But now we are getting stuck in the mfa/associate api.
curl --location 'https://client-domain/mfa/associate' \
--header 'content-type: application/json' \
--header 'authorization: Bearer ---------' \
--data '{ "authenticator_types": ["otp"] }'
We end up getting the ‘Invalid audience error‘. The token sent in this api is the mfa token generated after doing a mfa authentication with an existing method for the user.
{
"https://highbeam.co/user": {
"firstName": "Khushbu",
"guid": "xyz",
"lastName": "Goyal"
},
"iss": "https://custom-domain/",
"sub": "auth0|689d6b2e53877189833abb57",
"aud": [
"https://client-domain/mfa/",
"https://client-domain/userinfo"
],
"iat": 1766154335,
"exp": 1766154935,
"scope": "openid profile email enroll read:authenticators remove:authenticators",
"azp": "evZM4OfzLsyDcdg1rJPrsFMogCAP0NLl"
}
This is what the auth token looks like.
Can you please help with what we might be doing wrong ? Or how associate api can be called using Universal flow and without ROPG?
khushbu
December 19, 2025, 6:08pm
4
@gerald.czifra sorry for the direct ping, but will be able to help on this ?
Hi @khushbu ,
Welcome back to the Auth0 Community
Unfortunately calling the mfa/authenticators endpoint from a front-end application is not feasible at the moment, since there is a backlog item that our engineers are still working on, so indeed calling it from a back-end is the solution at the moment.
When it comes to your call to the /mfa/associate please make sure that the audience passed in the request is associated with your canonical domain and not your custom domain, so the correct audience would be: YOUR_TENANT.REGION.auth0.com/mfa/
You can also get around using an MFA Token by passing an Access token with enrollment scope to the “mfa/associate” endpoint, as suggested in this community topic as well - Mfa association mfa-api with access token vs mfa token approach .
Thank you, and if you have further questions please let me know!
system
January 2, 2026, 11:07pm
6
This topic was automatically closed 14 days after the last reply. New replies are no longer allowed.