Overview
This article explains how to implement federated logout for an OpenID Connect (OIDC) application when Auth0 acts as a bridge to an upstream Security Assertion Markup Language (SAML) Identity Provider (IdP). This process, also known as Single Logout (SLO), ensures that when a user logs out of the application, their session is also terminated with the upstream SAML IdP.
Applies To
- OpenID Connect (OIDC)
- SAML Enterprise Connections
- Federated Logout
- Single Logout (SLO)
Cause
In a federated identity scenario, there are multiple session layers: the application session, the Auth0 session, and the upstream IdP session. A standard logout from an OIDC application will only clear the local application and Auth0 sessions. To log the user out of the upstream SAML IdP, a federated logout must be explicitly initiated.
Solution
To implement a federated logout, the OIDC application must trigger the Auth0 logout endpoint with a specific parameter, and the SAML connection in Auth0 must be configured to communicate with the IdP’s logout endpoint.
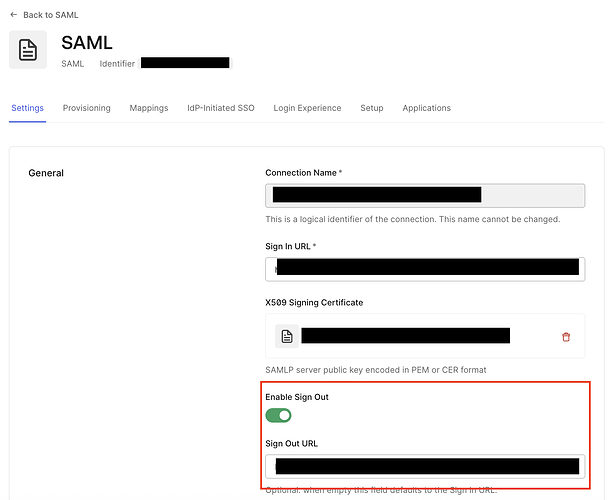
Step 1: Configure the SAML Connection in Auth0
Ensure that the SAML Enterprise Connection in Auth0 is configured for Single Logout (SLO).
- Navigate to the Auth0 Dashboard.
- Go to Authentication > Enterprise and select SAML.
- Choose the SAML connection that corresponds to the upstream IdP.
- In the connection’s Settings, enable the Sign Out toggle.
- In the Sign Out URL field, enter the single logout endpoint URL provided by the SAML IdP.
- Select Save Changes.
Step 2: Initiate Logout from the OIDC Application
The application is responsible for terminating its own local session and then redirecting the user to the Auth0 logout endpoint.
- Clear the Application Session: In the application code, remove the user’s session data (e.g., clear session cookies, remove tokens from local storage).
- Redirect to Auth0 Federated Logout Endpoint: After clearing the local session, redirect the user’s browser to the Auth0
/v2/logoutendpoint and include thefederatedquery string parameter.- Logout URL:
https://<YOUR_AUTH0_DOMAIN>/v2/logout?federated&client_id=<YOUR_CLIENT_ID>&returnTo=<URL_TO_REDIRECT_TO_AFTER_LOGOUT>
- Logout URL:
When Auth0 receives this request, it performs the following actions:
- Terminates the user’s Auth0 session.
- Redirects the user to the Sign Out URL configured in the SAML connection, initiating the logout process with the upstream IdP.
- After the IdP completes its logout process, the user is redirected back to the URL specified in the
returnToparameter.
NOTE: The returnTo URL must be registered in the Allowed Logout URLs list in either the Tenant Settings or the specific Application Settings in the Auth0 Dashboard.